With Cybersecurity risk management at the forefront, this paragraph opens a window to an amazing start and intrigue, inviting readers to embark on a storytelling casual formal language style filled with unexpected twists and insights.
Cybersecurity risk management is a critical aspect of protecting organizations from digital threats. From assessing risks to implementing robust frameworks, this comprehensive guide delves into the key components of safeguarding your data and systems.
Risk Assessment
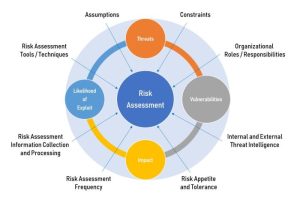
Conducting a thorough risk assessment is a crucial step in cybersecurity risk management as it helps organizations identify, analyze, and prioritize potential risks to their information systems and data. By understanding these risks, organizations can develop effective strategies to mitigate and manage them, thus enhancing their overall security posture.
Tools and Methodologies
There are various tools and methodologies used in the risk assessment process in cybersecurity. Some common ones include:
- Vulnerability Scanning: This involves scanning networks, systems, and applications to identify potential vulnerabilities that attackers could exploit.
- Penetration Testing: Also known as ethical hacking, this involves simulating real cyber attacks to identify weaknesses in an organization’s defenses.
- Risk Matrices: These tools help organizations prioritize risks based on likelihood and impact, allowing them to focus on the most critical threats.
Identifying Vulnerabilities and Threats
Identifying vulnerabilities and threats is a key aspect of risk assessment in cybersecurity. Vulnerabilities refer to weaknesses in systems or processes that could be exploited by attackers, while threats are potential events or incidents that could cause harm to an organization’s assets. By identifying and understanding these vulnerabilities and threats, organizations can proactively address security gaps and strengthen their defenses.
Risk Management
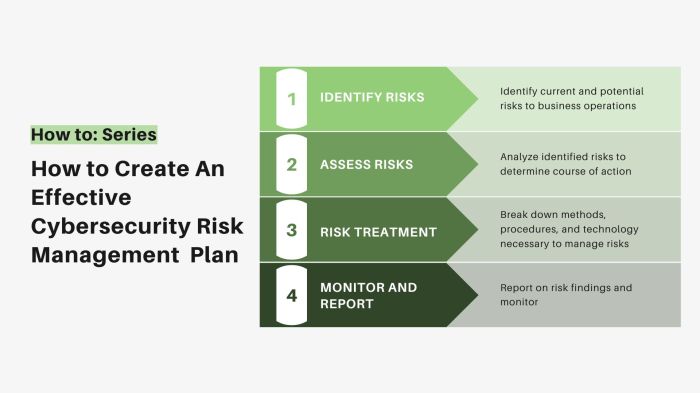
In the realm of cybersecurity, risk management plays a crucial role in safeguarding sensitive data and systems from potential threats. It involves identifying, assessing, and mitigating risks to minimize the impact of cyber attacks and breaches.
Strategies for Mitigating Cybersecurity Risks Effectively
Effective strategies for mitigating cybersecurity risks include:
- Implementing robust access controls to limit unauthorized access to systems and data.
- Regularly updating software and systems to patch vulnerabilities and enhance security.
- Conducting regular security awareness training for employees to educate them on best practices and potential threats.
- Using encryption to protect data both at rest and in transit.
- Deploying intrusion detection and prevention systems to detect and respond to cyber threats in real-time.
Importance of Creating a Risk Management Plan for Organizations
Creating a risk management plan is essential for organizations to:
- Identify and prioritize potential risks to their systems and data.
- Establish clear protocols and procedures for responding to security incidents.
- Allocate resources effectively to address high-priority risks and vulnerabilities.
- Ensure compliance with industry regulations and standards related to cybersecurity.
Risk Tolerance
Risk tolerance in cybersecurity refers to the level of risk that an organization is willing to accept or tolerate before taking action to mitigate it. It plays a crucial role in cybersecurity risk management as it helps organizations make informed decisions about which risks to address and how to allocate resources effectively.
Significance of Risk Tolerance
Risk tolerance is significant in cybersecurity risk management as it allows organizations to prioritize their efforts based on the level of risk they are willing to accept. By defining risk tolerance levels, organizations can align their cybersecurity strategies with their overall business goals and objectives. This helps in ensuring that resources are allocated efficiently and effectively to address the most critical risks.
Examples of Varying Risk Tolerance Levels
- In the financial industry, where data security and privacy are paramount, organizations tend to have low risk tolerance levels. Any breach or loss of sensitive information can have severe financial and reputational consequences.
- In the healthcare sector, hospitals and healthcare providers may have a moderate risk tolerance level as they deal with sensitive patient data. While the protection of patient information is crucial, they may prioritize patient care and operational efficiency.
- In the technology industry, where innovation and agility are key, organizations may have a higher risk tolerance level. They may be more willing to take risks to stay ahead of competitors and drive growth.
Relationship between Risk Tolerance and Decision-Making
Risk tolerance directly influences decision-making in cybersecurity. Organizations with a low risk tolerance are more likely to invest heavily in preventative measures and security controls to minimize risks. On the other hand, organizations with a higher risk tolerance may focus on rapid innovation and accept a certain level of risk as they pursue their business objectives. Understanding risk tolerance helps organizations make informed decisions about where to invest resources and how to balance security with business needs.
Risk Management Frameworks

When it comes to managing cybersecurity risks, organizations often rely on established frameworks to guide their efforts. These frameworks provide a structured approach to identifying, assessing, and mitigating risks, helping organizations strengthen their overall security posture.
In the realm of cybersecurity, there are several common risk management frameworks that organizations can leverage. Let’s explore some of the key frameworks and how they compare to each other.
NIST Cybersecurity Framework
- The NIST Cybersecurity Framework, developed by the National Institute of Standards and Technology, provides a flexible and risk-based approach to managing cybersecurity risks.
- It consists of five core functions – Identify, Protect, Detect, Respond, and Recover – which help organizations establish a comprehensive cybersecurity program.
- Organizations can use the NIST framework to assess their current cybersecurity posture, identify gaps, and prioritize areas for improvement.
ISO 27001
- ISO 27001 is an international standard that sets out the requirements for establishing, implementing, maintaining, and continually improving an information security management system.
- It provides a systematic approach to managing sensitive company information, ensuring its confidentiality, integrity, and availability.
- Organizations can achieve ISO 27001 certification by implementing an information security management system that meets the standard’s requirements.
How Organizations Can Leverage Risk Management Frameworks
- By adopting a risk management framework, organizations can establish a structured approach to identifying and addressing cybersecurity risks.
- Frameworks provide a common language and methodology for assessing risks, enabling organizations to prioritize their mitigation efforts effectively.
- Organizations can use risk management frameworks to align their cybersecurity initiatives with industry best practices and regulatory requirements, enhancing their overall security posture.
In conclusion, Cybersecurity risk management is a dynamic process that requires constant vigilance and strategic planning. By understanding the importance of risk assessment, risk management strategies, and the role of risk tolerance, organizations can effectively fortify their defenses against cyber threats. Stay informed, stay secure.
General Inquiries
What is the importance of risk assessment in cybersecurity risk management?
Risk assessment helps organizations identify potential vulnerabilities and threats, allowing them to prioritize resources and implement necessary security measures.
How can organizations mitigate cybersecurity risks effectively?
Organizations can mitigate cybersecurity risks by implementing robust security measures, conducting regular audits, and staying updated on the latest threats and vulnerabilities.
What is risk tolerance and why is it important in cybersecurity risk management?
Risk tolerance refers to an organization’s willingness to accept risks. Understanding risk tolerance helps in making informed decisions about cybersecurity investments and strategies.