In today’s digital landscape, Cybersecurity risk assessment plays a vital role in protecting organizations from cyber threats. This essential process helps identify vulnerabilities, assess risks, and prevent potential security breaches, ensuring a secure operational environment.
As we delve deeper into this topic, we will explore the critical components of Cybersecurity risk assessment, the risk assessment process, effective risk management strategies, and more.
Importance of Cybersecurity Risk Assessment
Implementing cybersecurity risk assessment is crucial for organizations to protect their sensitive data and assets from various cyber threats.
Identification of Vulnerabilities and Threats
Cybersecurity risk assessment plays a vital role in identifying vulnerabilities and potential threats that could compromise the security of an organization’s systems and data. By conducting a thorough assessment, organizations can pinpoint weak points in their security measures and take proactive steps to address them before an actual breach occurs.
Real-World Incidents
- In 2017, Equifax, a major credit reporting agency, suffered a massive data breach that exposed the personal information of over 147 million individuals. The breach was attributed to a failure in patching a known vulnerability, highlighting the importance of regular risk assessments to detect and address such vulnerabilities.
- In 2020, the SolarWinds cyberattack compromised numerous government agencies and corporations by exploiting a vulnerability in the company’s software supply chain. This incident underscored the critical need for organizations to assess the risks associated with third-party vendors and supply chain dependencies.
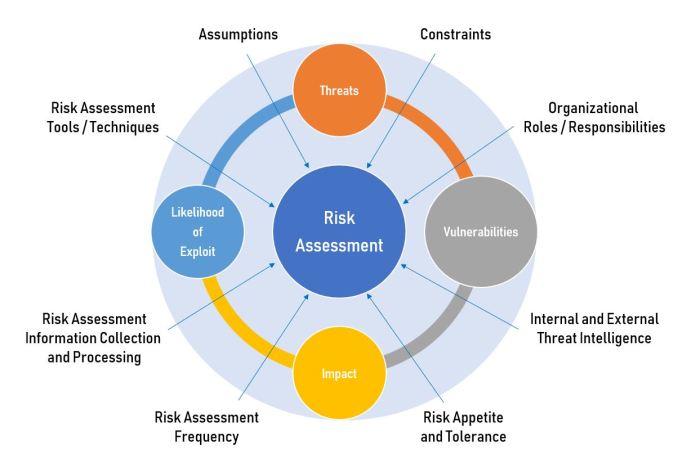
Components of a Cybersecurity Risk Assessment
When conducting a cybersecurity risk assessment, there are several key components that need to be considered to ensure the security of an organization’s digital assets.
Identify and Assess Assets
- Identify all assets, including hardware, software, data, and personnel, that need to be protected.
- Assess the value and importance of each asset to determine potential risks.
Threat Identification
- Identify potential threats that could exploit vulnerabilities in the system.
- Consider external threats like hackers, malware, and phishing attacks, as well as internal threats like employee errors or malicious insiders.
Vulnerability Assessment
- Conduct vulnerability assessments to identify weaknesses in the system that could be exploited by threats.
- Use tools like vulnerability scanners or penetration testing to uncover vulnerabilities.
Risk Analysis
- Analyze the likelihood of a threat exploiting a vulnerability and the impact it would have on the organization.
- Assign a risk level to each identified risk based on severity and potential impact.
Risk Mitigation
- Develop a plan to mitigate the identified risks, prioritizing those with the highest impact and likelihood of occurrence.
- Implement security controls, policies, and procedures to reduce the risk of a successful cyber attack.
Risk Assessment Process

In conducting a cybersecurity risk assessment, it is crucial to follow a structured step-by-step process to ensure comprehensive coverage of potential risks and vulnerabilities. This process involves defining assets, threats, vulnerabilities, and assessing the likelihood and impact of identified risks.
Defining Assets, Threats, Vulnerabilities, and Impact
When initiating a cybersecurity risk assessment, it is essential to first define the assets within the organization that need protection. These assets can include sensitive data, intellectual property, hardware, software, and network infrastructure. Identifying and categorizing these assets helps in understanding their value and the level of protection required.Next, it is crucial to identify potential threats that could exploit vulnerabilities within the organization’s systems.
Threats can come in the form of malicious actors, natural disasters, human error, or technical failures. Understanding the various threats enables organizations to prioritize risks and allocate resources effectively.Vulnerabilities refer to weaknesses in the organization’s security posture that could be exploited by threats. These vulnerabilities can exist in software, hardware, processes, or human behavior. By identifying vulnerabilities, organizations can implement remediation measures to reduce the likelihood of exploitation.Assessing the impact of identified risks involves evaluating the potential consequences of a successful cyber attack.
This assessment considers the financial, operational, reputational, and regulatory implications of a security breach. Understanding the impact helps organizations prioritize risk mitigation efforts and allocate resources appropriately.
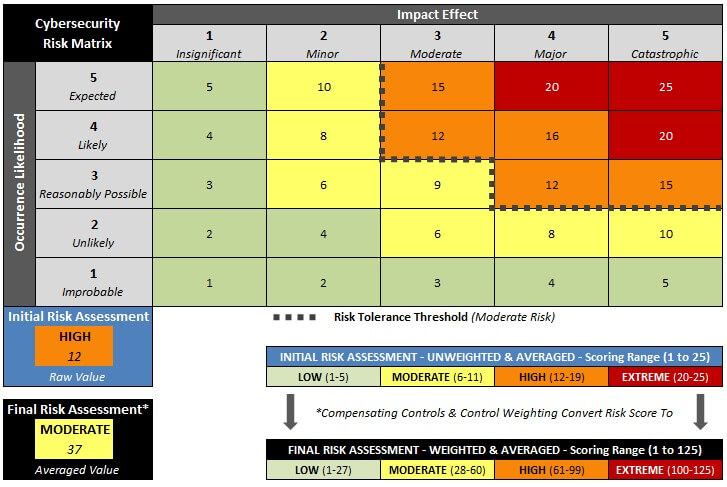
Assessing Likelihood and Impact of Risks
Once assets, threats, vulnerabilities, and impact have been defined, the next step is to assess the likelihood and impact of identified risks. This involves evaluating the probability of a threat exploiting a vulnerability and the severity of the consequences if a security breach occurs.To assess the likelihood of risks, organizations can utilize historical data, threat intelligence, risk assessment frameworks, and expert judgment.
By quantifying the likelihood of different risks, organizations can prioritize mitigation efforts based on the level of threat they pose.Assessing the impact of risks involves estimating the potential financial, operational, reputational, and regulatory consequences of a security breach. Organizations can use impact assessment tools, scenario analysis, and business impact analysis to quantify the potential impact of different risks accurately.By systematically assessing the likelihood and impact of identified risks, organizations can develop a risk management strategy that focuses on mitigating the most critical threats effectively.
This proactive approach helps organizations strengthen their cybersecurity defenses and protect their valuable assets from cyber threats.
Risk Management Strategies
After conducting a cybersecurity risk assessment, organizations must implement effective risk management strategies to address and mitigate potential risks. These strategies are crucial in safeguarding sensitive information and maintaining the integrity of their systems and data.
Risk Tolerance and Decision-making
One key concept in risk management is risk tolerance, which refers to the level of risk that an organization is willing to accept before taking action. This tolerance level influences decision-making processes in risk management, guiding organizations on how to prioritize and address different risks identified in the assessment.
Mitigation Techniques
- Implementing Strong Access Controls: Limiting access to sensitive data and systems only to authorized personnel can help prevent unauthorized access and reduce the risk of data breaches.
- Regular Security Training: Educating employees on cybersecurity best practices and potential threats can help create a security-conscious culture within the organization, reducing the likelihood of human errors leading to security incidents.
- Using Multi-factor Authentication: Adding an extra layer of security through multi-factor authentication can enhance the protection of user accounts and prevent unauthorized access even if login credentials are compromised.
- Regular Software Updates and Patch Management: Keeping software and systems up to date with the latest security patches can help address known vulnerabilities and protect against potential cyber threats exploiting these weaknesses.
- Incident Response Planning: Developing and testing an incident response plan can help organizations effectively respond to cybersecurity incidents, minimizing the impact and reducing recovery time.
As we conclude our discussion on Cybersecurity risk assessment, it becomes evident that a proactive approach to risk assessment is paramount in safeguarding organizations from evolving cyber threats. By understanding the importance of risk assessment, implementing robust strategies, and staying vigilant, organizations can strengthen their cybersecurity posture and protect valuable assets.
Essential FAQs
What is the significance of conducting a cybersecurity risk assessment?
A cybersecurity risk assessment is crucial as it helps organizations identify vulnerabilities, assess threats, and take proactive measures to prevent security breaches.
How can organizations prioritize risks during a cybersecurity risk assessment?
Organizations can prioritize risks based on severity and potential impact on critical assets and operations, ensuring that resources are allocated effectively.
What are some common risk management strategies based on the results of a risk assessment?
Organizations can implement strategies such as risk avoidance, risk transfer, risk mitigation, or risk acceptance to address identified cybersecurity risks.






